Cybercrime costs small businesses more than $2.2 million on average each year. With threats growing smarter and attacks becoming more frequent, simply having a website is not enough. Building a secure online presence starts with understanding your risks and ends with rigorous protection at every step. This guide shows you practical strategies that safeguard your business while giving you the confidence to grow online.
Table of Contents
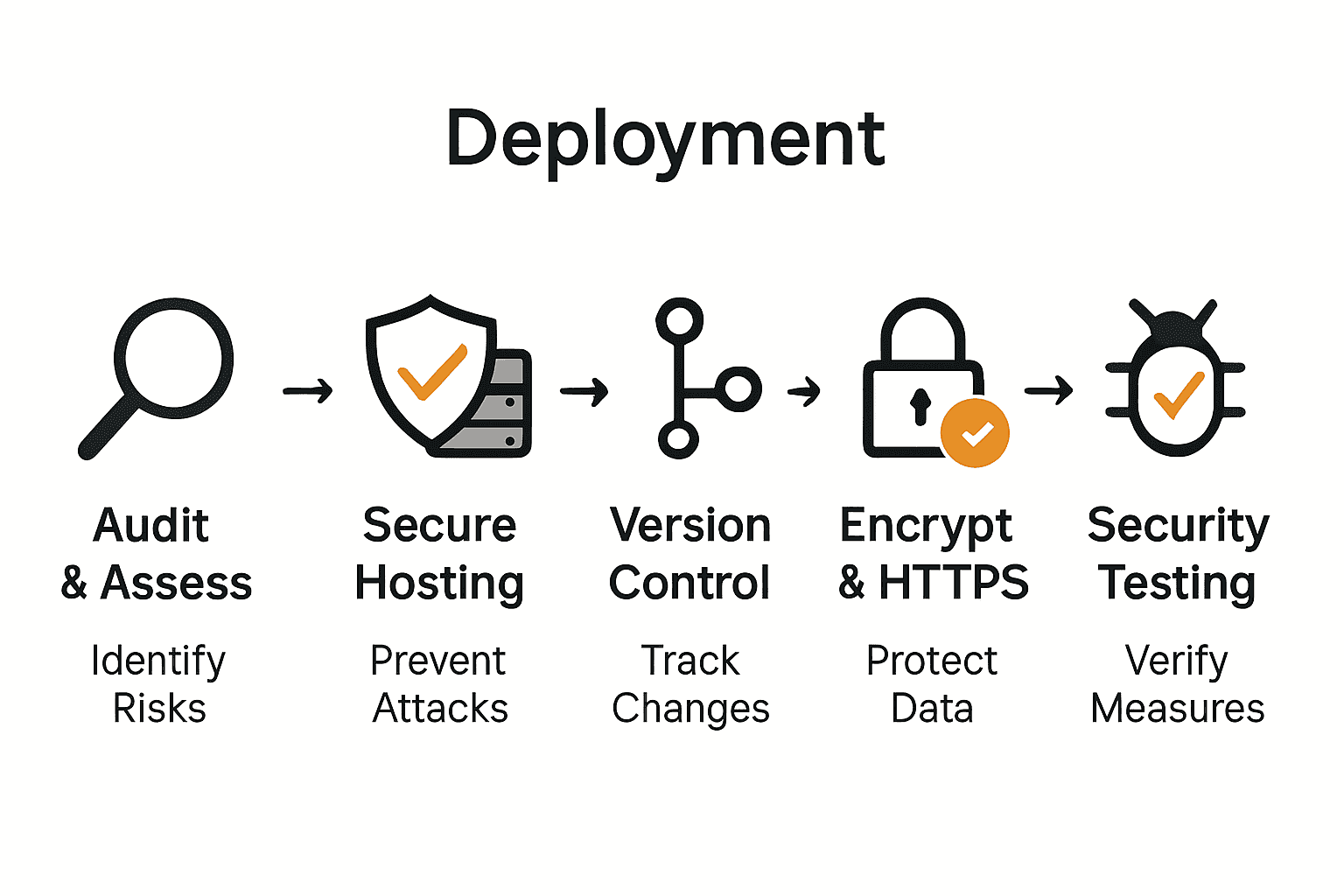
- Step 1: Assess Security Vulnerabilities And Requirements
- Step 2: Configure Secure Hosting Environments
- Step 3: Deploy Code With Version Control Best Practices
- Step 4: Implement Https And Encryption Measures
- Step 5: Test And Verify Website Security Post-Deployment
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Identify security vulnerabilities systematically | Conduct a thorough audit of your digital landscape to identify specific risks and create a tailored security strategy. |
| 2. Choose a secure hosting provider | Select a hosting service with advanced security features like firewalls and DDoS protection to protect your digital assets. |
| 3. Implement strong version control practices | Use tools like Git and establish code review processes to secure your software development and deployment workflows. |
| 4. Enforce HTTPS and encryption | Install SSL certificates and configure HTTPS to encrypt data transmission, protecting sensitive information from unauthorized access. |
| 5. Conduct thorough security testing post-deployment | Perform dynamic and static security testing to identify and address vulnerabilities that may have arisen during deployment. |
Step 1: Assess security vulnerabilities and requirements
In this crucial step, you will systematically identify potential security risks unique to your business infrastructure. By carefully examining your digital landscape, you can create a targeted security strategy that protects your most valuable assets.
According to research from arXiv, small businesses must develop a structured approach to understanding their cybersecurity risks. The Small IT Data (SITD) model suggests mapping out your organisational vulnerabilities by considering your specific business context. Start by conducting a comprehensive audit that covers:
- Hardware inventory and network infrastructure
- Software applications and their potential entry points
- User access privileges and authentication mechanisms
- Data storage and transmission protocols
To make this process more effective, arXiv recommends evaluating your cybersecurity competence through a systematic classification framework. This means looking beyond generic security checklists and tailoring your assessment to your organisation’s unique operational needs.
Pro Tip: Do not attempt to address every possible vulnerability simultaneously. Prioritise risks based on potential business impact and available resources.
Once you complete this assessment, you will have a clear roadmap of your current security landscape and be ready to develop targeted mitigation strategies. The next step involves translating these insights into actionable security improvements that align with your business objectives.
Step 2: Configure secure hosting environments
In this critical step, you will establish a robust hosting environment that shields your website from potential security threats and ensures your digital infrastructure remains resilient against cyber attacks. Your goal is to create a fortified digital foundation that protects your business data and customer information.
GoDaddy emphasizes the importance of selecting a web hosting provider with comprehensive security measures. When configuring your hosting environment, prioritise providers that offer:
- Advanced firewall protection
- Intrusion detection systems
- Regular security updates
- Secure server configurations
- Automated backup solutions
According to SSLs, small businesses should specifically look for hosting services that provide web application firewalls (WAF) and DDoS protection. These features act as powerful shields against common online threats, preventing unauthorized access and potential service disruptions.
Pro Tip: Always choose a hosting provider that offers 24/7 technical support and has a transparent security incident response plan.
Once you have configured your secure hosting environment, you will have established a strong first line of defence for your digital presence. The next step involves implementing additional layers of security to further fortify your website against potential vulnerabilities.

Step 3: Deploy code with version control best practices
In this crucial step, you will learn how to implement robust version control practices that ensure your software development process remains secure, traceable, and efficient. Your goal is to create a systematic approach to code deployment that minimizes risks and maximizes reliability.
Wikipedia highlights the importance of Software Composition Analysis (SCA) in modern code deployment. This means carefully examining all software components particularly open-source elements to verify they are current and free from potential security vulnerabilities. When setting up your version control workflow, consider these key strategies:
- Use a distributed version control system like Git
- Create separate branches for development testing and production
- Implement comprehensive code review processes
- Integrate automated security scanning tools
- Maintain detailed commit logs and documentation
According to Wikipedia, Static Application Security Testing (SAST) provides an additional layer of protection by systematically reviewing source code to identify potential security weaknesses before deployment. This proactive approach allows you to catch and resolve vulnerabilities early in the development cycle.
Pro Tip: Never commit sensitive information like passwords or API keys directly into your version control system. Use secure environment variables or dedicated secret management tools.
Once you have established these version control best practices, you will have created a robust framework for secure and efficient code deployment. The next step involves setting up continuous integration and continuous deployment (CI/CD) pipelines to further streamline your development process.
Step 4: Implement HTTPS and encryption measures
In this crucial step, you will protect your website and customer data by implementing robust encryption protocols that prevent unauthorized access and secure sensitive information. Your objective is to create a digital fortress that shields your online presence from potential cyber threats.
SSLs emphasizes the critical importance of installing SSL certificates to encrypt data transmission between your website and its users. This process involves several key actions:
- Purchase a reputable SSL certificate from a trusted certificate authority
- Configure your web server to enable HTTPS
- Redirect all HTTP traffic to HTTPS automatically
- Implement strong encryption protocols like TLS 1.2 or 1.3
- Regularly update and renew your SSL certificates
According to Userlike, implementing Secure Socket Layer encryption prevents hackers from intercepting sensitive data during transmission. This means that any information exchanged between your website and users remains confidential and protected from potential malicious interception.
Pro Tip: Choose an SSL certificate that provides extended validation for maximum trust and visibility. Green address bars and trust seals can significantly boost customer confidence.
Once you have successfully implemented HTTPS and encryption measures, you will have established a secure communication channel that protects both your business and your customers. The next step involves implementing additional security layers to further fortify your digital infrastructure.
Step 5: Test and verify website security post-deployment
In this critical step, you will systematically evaluate your website’s security infrastructure to ensure comprehensive protection against potential cyber threats. Your primary objective is to conduct thorough security testing that identifies and mitigates any vulnerabilities that might have emerged during deployment.
Wikipedia highlights the importance of Dynamic Application Security Testing (DAST), which involves examining a live application to uncover potential security weaknesses. When performing post-deployment verification, focus on these key testing strategies:
- Conduct comprehensive penetration testing
- Scan for potential vulnerabilities using automated security tools
- Test all user authentication and access control mechanisms
- Verify encryption protocols and data transmission security
- Simulate potential cyber attack scenarios
Additionally, Wikipedia recommends integrating Static Application Security Testing (SAST) techniques to review source code and identify potential security flaws. This dual approach of dynamic and static testing provides a robust method for ensuring your website’s security posture remains strong.
Pro Tip: Schedule regular security audits and consider engaging professional cybersecurity experts to perform independent assessments of your website’s security infrastructure.
Once you have completed these comprehensive security tests, you will have established a reliable framework for ongoing website protection. For an even more seamless migration process, check out our site migration checklist to ensure every aspect of your digital infrastructure remains secure and optimised.
Strengthen Your Website Security with Smarter Automation Solutions
Deploying a secure website requires more than just technical steps like HTTPS implementation and version control. Small businesses face real challenges managing complex security demands while trying to keep operations smooth and scalable. If you are feeling overwhelmed prioritising security vulnerabilities or configuring a robust hosting environment, you are not alone. The right blend of automation and intelligent systems can transform these manual struggles into seamless, reliable processes.
At Fame Razak, we understand the pressure of safeguarding your digital presence while focusing on growth. Our approach as a Fractional CTO integrates AI-powered workflow orchestration and automation tailored precisely for small business needs. This means you can automate security checks, streamline deployment procedures, and maintain continuous protection without the stress of juggling multiple tools. Ready to move beyond basic security steps and future-proof your website with intelligent automation Discover how our solutions can help you maintain a secure, scalable environment today. Explore more at Fame Razak and take the first step toward turning website security challenges into automated strengths.
Frequently Asked Questions
What are the first steps to assess vulnerabilities in my small business’s website?
Begin by conducting a comprehensive audit of your hardware, software, user access, and data management practices. Create a list of potential security risks specific to your business, and prioritize them based on their potential impact.
How can I configure a secure hosting environment for my small business website?
Choose a hosting provider that offers advanced firewall protection, regular security updates, and automated backups. Ensure your server configurations are secure and that you have access to 24/7 technical support to handle any emergencies.
What version control best practices should I implement for secure code deployment?
Utilize a distributed version control system to manage your code. Implement separate branches for development and production, and integrate automated security scanning tools to identify vulnerabilities before deployment.
How can I ensure my website uses HTTPS and strong encryption measures?
Purchase an SSL certificate from a trusted authority and configure your web server to enable HTTPS. Automatically redirect all HTTP traffic to HTTPS to secure data transmission and use strong encryption protocols, like TLS 1.2 or 1.3.
What steps should I take to test my website’s security after deployment?
Conduct thorough penetration testing and utilize automated security tools to scan for vulnerabilities. Verify user authentication and access controls, and simulate potential cyber-attack scenarios to ensure your site is protected from threats.
How often should I perform security audits on my small business website?
Schedule security audits at least every six months to ensure your website’s protection remains effective. Additionally, conduct audits after significant changes or updates to your site to catch any new vulnerabilities immediately.
